Medical Records
HIPAA is the acronym for the Health Insurance Portability and Accountability Act of 1996. The Act requires The Department of Health and Human Services to develop regulations to protect the privacy and security of identifiable health information. Two sets of regulations, referred to as the Privacy Rule and Security Rule, outline the requirements that must be followed when entities subject to the rules use and share health information. When research involves the use or disclosure of protected health information (PHI) by entities subject to the regulations, the rules will apply.
In This Section
- HIPAA Basics for Researchers
- What Types of Information are Regulated by HIPAA?
- The 18 HIPAA Identifiers
- When Does HIPAA Apply to Research?
- How Do I Comply with HIPAA as a Researcher?
- How Do I Request a HIPAA Waiver?
- Research Involving De-Identified Health Information
- Data Use Agreements and Limited Data Sets
Related Topics
- De-identification of PHI
- The University of California HIPAA website
- NIH: Understanding the HIPAA Privacy Rule website
- Access to PHI on Decedent Information (UCDHS Compliance Program)
HIPAA Basics for Researchers
The Health Insurance Portability and Accountability Act of 1996 (HIPAA) required the Department of Health and Human Services (HHS) to develop regulations to protect the privacy and security of identifiable health information. As a result of this requirement, HHS issued two sets of regulations, the Privacy Rule and the Security Rule. These rules apply to covered entities and their business associates.
What is a covered entity?
A covered entity is a health care provider, health plan, or health care clearinghouse that transmits any health information in connection with a financial transaction.
Health Care Provider
This includes providers such as:
- Doctors
- Clinics
- Psychologists
- Dentists
- Nursing homes
- Pharmacies
- Health systems
Health Plan
This includes:
- Health insurance companies
- Health maintenance organizations (HMOs)
- Company health plans
- Government programs that pay for health care, such as Medicare, Medicaid, and military health care program
Health Care Clearinghouse
This includes entities that facilitate payment for health care services by processing nonstandard data into a standard format or vice versa, such as:
- Billing services
- Repricing companies
- Community health management information systems
What Types of Information are Regulated by HIPAA?
The Privacy Rule and Security Rule apply to Protected Health Information (PHI). PHI is defined as individually identifiable health information that is maintained or transmitted in any form or medium (e.g., electronic, oral, or paper) by a covered entity or its business associates, excluding certain educational and employment records.
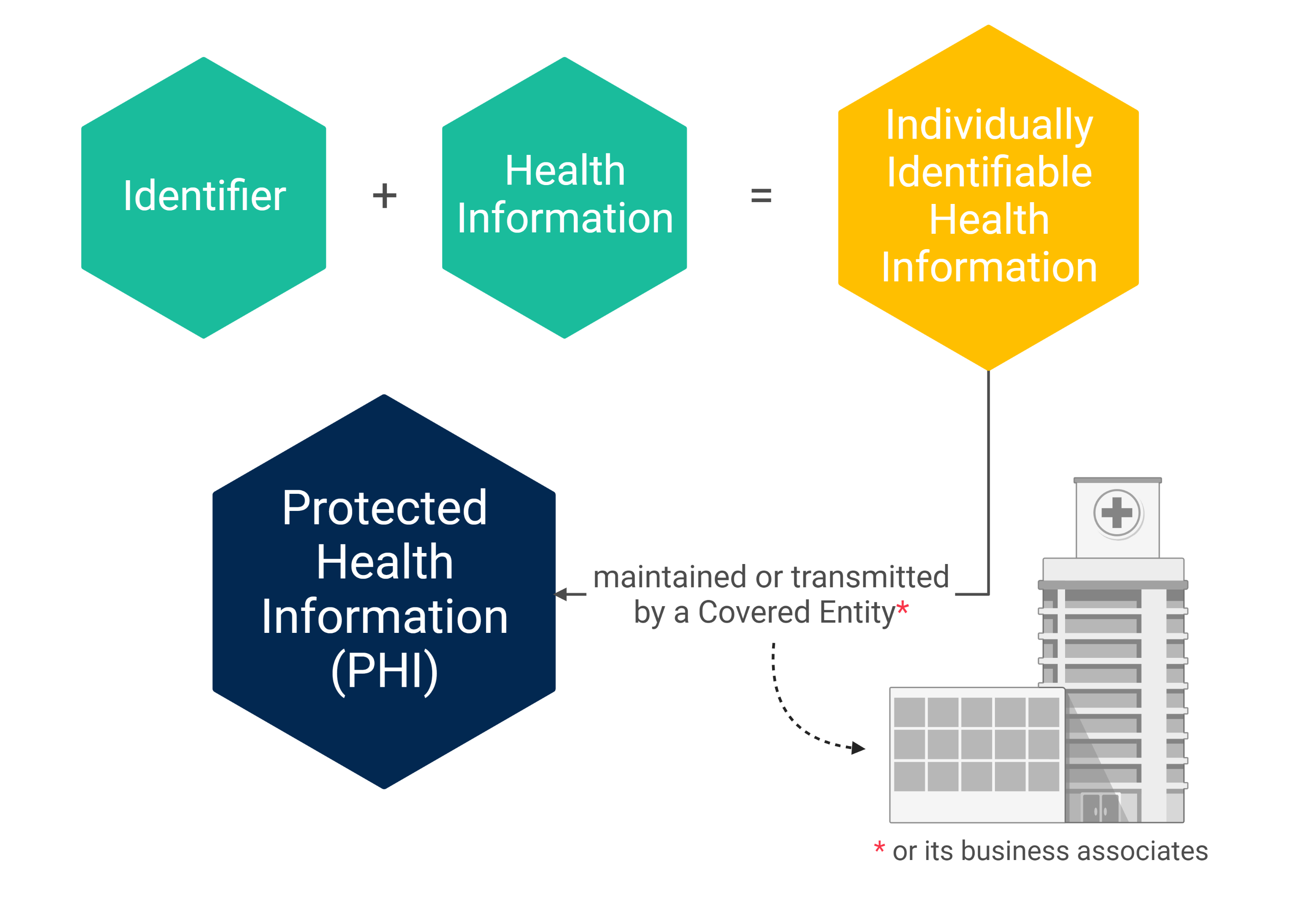
The 18 HIPAA Identifiers
In most instances, health information is considered individually identifiable when any of the following identifiers are included with the information:
- Names
- Telephone numbers
- Fax numbers
- Email addresses
- Social Security numbers
- Medical record numbers
- Health plan beneficiary
- Vehicle identifiers and serial numbers, including license plate numbers
- Account numbers
- Certificate/license numbers
- Device identifiers and serial numbers
- Web Universal Resource Locators (URLs)
- Internet Protocol (IP) addresses
- Biometric identifiers, including finger and voice prints
- Full-face photographs and any comparable images
- Any other unique identifying number, characteristic, or code
- A unique identifying number, characteristic, or code is NOT considered an identifier if permitted by the Privacy Rule for re-identification (e.g., a subject ID number).
- All elements of dates (except year) for dates that are directly related to an individual
- Dates related to an individual include:
- Birth date
- Dates associated with health care services (e.g., admission date, procedure date, and discharge date)
- Death date
- All ages over 89 and elements of dates (including year) indicative of such age, except when such ages and elements are aggregated into a single category of age 90 or older
- Dates related to an individual include:
- All geographic subdivisions smaller than a state
- Geographic subdivisions that are considered identifiers include:
- Street address
- City
- County
- Precinct
- ZIP code*
- Equivalent geocodes
- Geographic subdivisions that are considered identifiers include:
* The initial three digits of the ZIP code are not considered an identifier if, according to the current publicly available data from the Bureau of the Census, the geographic unit formed by combining all ZIP codes with the same three initial digits contains more than 20,000 people; and the initial three digits of a ZIP code for all such geographic units containing 20,000 or fewer people is changed to 000.
Data that is derivative of any of the 18 HIPAA identifiers, such as initials or a partial medical record number, are considered indirect identifiers. If a data set includes indirect identifiers, it is considered identifiable.
When Does HIPAA Apply to Research?
When research involves creation, use, or disclosure of protected health information (PHI) by UC Davis Health, HIPAA’s Privacy Rule and Security Rule apply. In general, there are two types of human research that involve PHI:
- Studies involving review of medical records as a source of research information
- Studies that create new medical information because a health care service is being performed as part of the research
How Do I Comply with HIPAA as a Researcher?
There are three main approaches researchers can take to comply with HIPAA. The appropriate approach depends on the study design of the research being conducted. The three approaches are as follows:
Signed UC HIPAA Research Authorization
When researchers follow this approach, all subjects or their legally authorized representatives (LARs) sign the UC HIPAA Research Authorization (University of California Permission to Use Personal Health Information for Research) at the time of consent.
The researcher may not access potential subjects’ medical records for research purposes until the subject has signed the informed consent form and HIPAA Research Authorization.
- IRB TIP: The HIPAA Research Authorization is available in multiple languages on the IRB Forms webpage.
Partial Waiver of HIPAA Authorization + UC HIPAA Research Authorization
When researchers are granted a Partial Waiver of HIPAA Authorization for participant identification and recruitment by the UC Davis IRB, the medical records of potential subjects may be accessed prior to obtaining a signed UC HIPAA Research Authorization for identification and recruitment purposes only.
If access to the subject’s medical record for research purposes beyond subject identification and recruitment, subjects or their legally authorized representatives (LARs) will still sign the UC HIPAA Research Authorization at the time of consent.
This approach is useful for clinical trials.
- IRB TIP: The HIPAA Research Authorization is available in multiple languages on the IRB Forms webpage.
Partial Waiver of HIPAA Authorization
When researchers are granted a Partial Waiver of HIPAA Authorization for participant identification and recruitment by the UC Davis IRB, the medical records of potential subjects may be accessed prior to obtaining a signed UC HIPAA Research Authorization for identification and recruitment purposes only.
If access to the subject’s medical record for research purposes beyond subject identification and recruitment, subjects or their legally authorized representatives (LARs) will still sign the UC HIPAA Research Authorization at the time of consent.
- IRB TIP: The HIPAA Research Authorization is available in multiple languages on the IRB Forms webpage.
Full Waiver of HIPAA Authorization
When researchers are granted a Full Waiver of HIPAA Authorization for the study by the UC Davis IRB, the researcher may access the medical records of subjects without obtaining a signed UC HIPAA Research Authorization (University of California Permission to Use Personal Health Information for Research).
This approach is useful for chart review studies.
- COMMON MISTAKE: If a Full Waiver of HIPAA Authorization is issued by the IRB, then the identifiable information may not be re-disclosed to anyone outside of the study team.
NOTE: UC Davis Health acknowledges that all information placed into the Electronic Health Record system (EPIC) by Marshall Medical Center (MMC) is the proprietary information of MMC, and shall not be accessed, used, and/or disclosed by UC Davis Health unless MMC specifically authorizes such.
How Do I Request a HIPAA Waiver?
It is always preferred to obtain authorization to use an individual’s PHI. However, researchers may request either a Partial or Full Waiver of HIPAA Authorization on the “HIPAA” page of the Initial Review Application on IRBNet. If a waiver is requested, researchers will then have the opportunity to provide the rationale for requesting a waiver on the following page.
In order to waive the requirement for an authorization, the IRB must determine that the study meets the following criteria:
- Use or disclosure involves no more than minimal risk to the privacy of individuals because of the presence of at least the following elements:
- An adequate plan to protect health information identifiers from improper use or disclosure
- An adequate plan to destroy identifiers at the earliest opportunity absent a health or research justification or legal requirement to retain them
- Adequate written assurances that the PHI will not be used or disclosed to a third party except as required by law, for authorized oversight of the research study, or for other research uses and disclosures permitted by the Privacy Rule
- Research could not practicably be conducted without the waiver or alteration
- Research could not practicably be conducted without access to and use of PHI
How Do I Determine if a Study Was Granted a HIPAA Waiver?
If a waiver of authorization is granted, the IRB will issue a HIPAA Waiver Notice with the approval documents on IRBNet.
- COMMON MISTAKE: Make sure to read the HIPAA Waiver Notice to ensure you were granted the type of HIPAA Waiver of Authorization you requested and review the details of the waiver.
Additional Information About the UC HIPAA Research Authorization
Electronic Signatures
If information about obtaining electronic consent is included in the approved informed consent form for a study, then DocuSign may be used to obtain signature on the UC HIPAA Research Authorization. If this language was omitted from the informed consent form, researchers may submit a modification to include it. Once approved, the use of DocuSign is allowed.
- COMMON MISTAKE: REDCap may not be used to obtain electronic signatures on the UC HIPAA Research Authorization.
Reliance Agreements
When UC Davis is relying on an external IRB, researchers must still use the UC HIPAA Research Authorization if a study requires a signed HIPAA authorization form. This form cannot be embedded within the informed consent form. Changes to the UC HIPAA Research Authorization will require negotiations with the Compliance Department.
For more information about how to comply with HIPAA in studies involving a reliance agreement, refer to the Single IRB and Reliances webpage.
Research Involving De-Identified Health Information
The Privacy Rule allows a covered entity or its business associates to use or disclose de-identified health information without restriction. There are two methods the covered entity (e.g., UC Davis Health) or its business associates may use to de-identify health information:
- Safe Harbor
- Expert Determination
Safe Harbor is the most common method used by UC Davis Health.
Safe Harbor
The Safe Harbor method allows the covered entity or its business associates to de-identify health information by removing the 18 HIPAA identifiers related to an individual or that individual’s relatives, employers, or household members. The covered entity or its business associates must have no actual knowledge that the remaining information could be used, alone or in combination with other information, to identify the individual whose health information is included in the data set.
The individual or system that removes the identifying data is oftentimes referred to as an honest broker. Honest brokers must meet the following criteria:
- The honest broker is not part of the research team.
- The honest broker has access to the desired data by virtue of their normal job functions.
- The honest broker will not receive professional recognition or publication privileges as part of the research.
Expert Determination
The Expert Determination method allows a covered entity or its business associates to utilize a person with appropriate knowledge of and experience with generally accepted statistical and scientific principles and methods for rendering information not individually identifiable. This expert is responsible for determining that there is only a very small risk that the anticipated recipient of the data set could use the provided information, alone or in combination with other reasonably available information, to identify individuals in the data set. Additionally, this person is responsible for documenting the methods and results of the analysis that justify such a determination.
For additional information on implementation of the Safe Harbor and Expert Determination methods, please see the HHS guidance on these topics.
Data Use Agreements and Limited Data Sets
The Privacy Rule allows a covered entity to use and disclose a limited data set for research activities if the covered entity and the data recipient enter into a Data Use Agreement.
What is a Limited Data Set?
A limited data set refers to PHI that excludes 16 of the 18 HIPAA identifiers and may be used or disclosed, for purposes of research, public health, or health care operations, without obtaining either an individual’s Authorization or a waiver or an alteration of Authorization for its use and disclosure, with a data use agreement.
Below is a list of identifiers that may be included in a limited data set:
- Dates that are directly related to an individual
- Age in months, days, or hours
- City and zip code
What is a Data Use Agreement (DUA)
A Data Use Agreement (DUA) is an agreement into which the covered entity enters with the intended recipient of a limited data set that establishes the ways in which the information in the limited data set may be used and how it will be protected.
The Data Use Agreement must contain the following provisions:
- The permitted use of the limited data set must be consistent with the purpose for which it was disclosed
- A DUA cannot authorize the recipient to use or further disclose the information in a way that, if done by the covered entity, would violate the Privacy Rule.
- Identification of who is permitted to use or receive the limited data set
- Stipulations that the recipient will
- Not use or disclose the information other than permitted by the agreement or otherwise required by law
- Use appropriate safeguards to prevent the use or disclosure of the information, except as provided for in the agreement, and require the recipient to report to the covered entity any uses or disclosures in violation of the agreement of which the recipient becomes aware
- Hold any agent of the recipient (including subcontractors) to the standards, restrictions, and conditions stated in the data use agreement with respect to the information
- Not identify the information or contact the individuals
Violations of the Data Use Agreement
If the recipient of the limited data set is a covered entity who violates the data use agreement, it is deemed a violation of the Privacy Rule. If the covered entity providing the limited data to a recipient notices patterns of a breach or violations of the agreement, the covered entity must take steps to correct the inappropriate activity. If steps taken by the covered entity are unsuccessful, the covered entity must discontinue disclosing the PHI to the recipient and notify the HHS.
Section 164.512 of the Privacy Rule also establishes specific PHI uses and disclosures that a covered entity is permitted to make for research without an Authorization, a waiver or an alteration of Authorization, or a data use agreement. These limited activities are the use or disclosure of PHI preparatory to research and the use or disclosure of PHI pertaining to decedents for research.
How Do I Obtain Permission to Use a Limited Data Set and DUA in Research?
Researchers who intend to enter into a DUA with an outside entity in order to disclose or receive a limited data set will indicate this intention on the “Ancillary Reviews” page of the Initial Review Application on IRBNet.
The Technology Transfer Office (TTO) has the authority to execute Data Use Agreements at UC Davis. It is the researcher’s responsibility to submit a DUA request to the TTO prior to disclosing or receiving a limited data set.

 Institutional Review Board
Institutional Review Board